
Hacktivists operating on the side of Ukraine have focused their DDoS attacks on a portal that is considered crucial for the distribution of alcoholic beverages in Russia.
DDoS (distributed denial of service) attacks are collective efforts to overwhelm servers with large volumes of garbage traffic and bogus requests, rendering them unable to serve legitimate visitors.
According to reports from multiple Russian media outlets, several vodka producers and distributors claim inability to access the EGAIS (ЕГАИС) portal as required by government regulations.
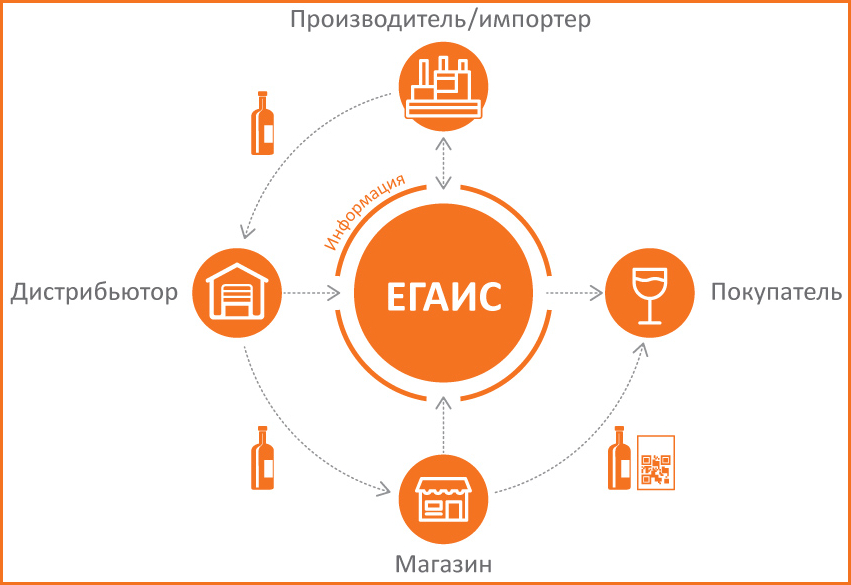
As a result, alcohol beverages transportation and distribution to retail points have suffered greatly in the past couple of days, raising the risk of actual shortages on the shelves.
A person working in the field told Vedomosti that “Due to a large-scale failure, factories cannot accept tanks with alcohol, and customers, stores, and distributors, can not receive finished products that have already been delivered to them.”
Yesterday, many factories decided to halt shipments to warehouses completely and subsequently cut their production rate, as they are overflowing with products that remain undelivered and can’t take any more.
Ukraine’s IT Army lists EGAIS
At the time of writing this, the portal of EGAIS remains out of reach, so we can only assume that the DDoS attack is still ongoing.
Bleeping Computer has found the associated websites listed as targets on Ukraine’s IT Army Telegram channel, so there’s a good chance that they are behind these attacks.
The posts on Telegram are meant to help coordinate DDoS activities that are launched independently from isolated actors using tools like the Liberator.
Ukraine's IT Army is a special type of a cyber-force that enlists volunteers from around the globe, uniting them under the common goal of launching retaliatory cyberattacks against key Russian entities.
The formation of this otherwise illegal task force was announced by Ukraine’s government officials in February 2022 and has remained active on the cyber front line since then.
Attacks on Russian supply chains
This is not the first attack targeting Russia’s internal product supply chains, aiming to cause disruption and potentially even shortages.
Last March, the Moscow-based meat producer, and distributor Miratorg announced news of a cyberattack that encrypted its IT systems, aiming to sabotage its operations.
The point of compromise was another state information system, VetIS, used by companies engaged in the veterinary field.



Comments
h_b_s - 1 year ago
I really doubt there's many people shedding a tear over this being illegal in most countries' criminal code. Russia is one of the countries that refused to play ball, now the rest of the world is fed up with them. China won't be far behind in being a target of vigilante justice like this. The cyberworld is about to go nuclear on each other.
Amigo-A - 1 year ago
There are no failures in work, all sites work fine.
UA lies as always, but they lie for the dollars that the USA pays them.
The bad news is that USA believes them and pays for what they don't do.
https://ibb.co/dMz6FYS
https://ibb.co/X3x13dw
rtp-020 - 1 year ago
hmm.
did you notice these quotes?
"According to reports from multiple Russian media outlets,... "
"A person working in the field told Vedomosti... "
this article is based on info provided by muscovite sources.
buddy215 - 1 year ago
Yep...Amigo-A is telling us not to believe our lying eyes.
2891 - 1 year ago
The Ukraine It Army is helping Russia to deal with it's serious problem of excess alcohol consumption. What genius Ukrainian came up with that one? The Russian government will probably allow this to go on as long as it can. Please PLEASE do not throw me into the briar patch!!