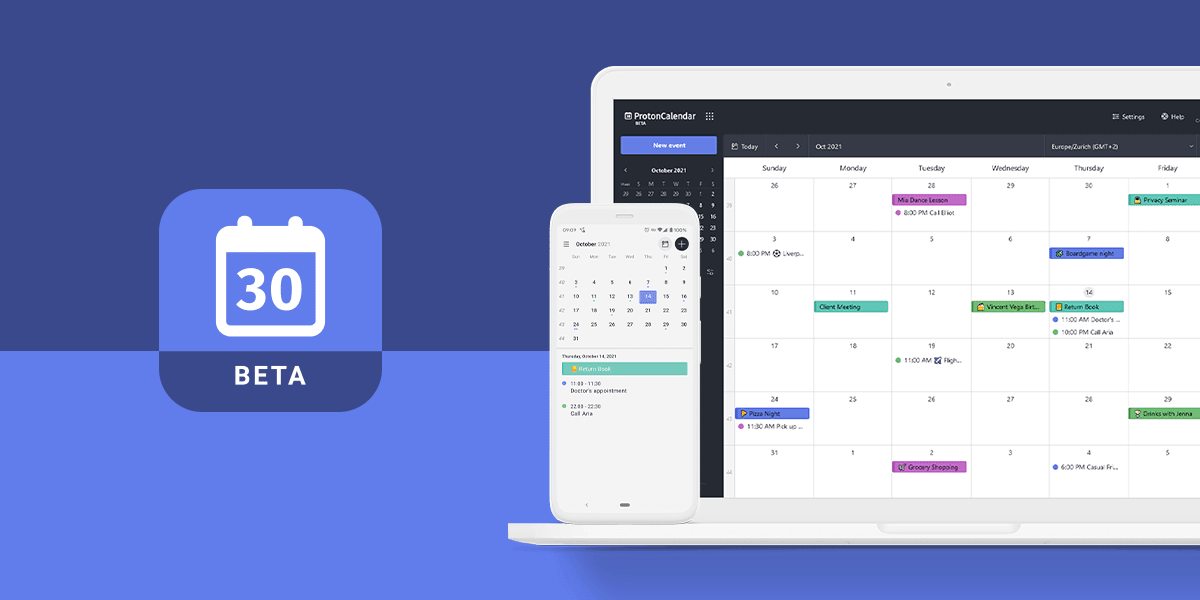
Proton Calendar(new window), our privacy-focused calendar app, is now available in beta on Android and web for everyone who has a Proton Account. Protected by the same end-to-end encryption used in Proton Mail, this simple, easy-to-use, and intuitive calendar will help you stay on top of your schedule while securing your data.
If you already have Proton Mail, you can try Proton Calendar beta on the web and Android devices (with the beta app for iOS coming soon).
You can access Proton Calendar beta on the web by going to calendar.proton.me(new window) and logging in with your Proton Mail credentials. Or you can log in to mail.proton.me(new window) and use the App Selector.

You can download the Proton Calendar Android app beta from the Play Store.
Stay on top of your schedule with Proton Calendar beta
We’ve built Proton Calendar from the ground up, so you can spend less time managing your day and more time enjoying it. It takes a lot of work to stay on top of your schedule, which is why we’ve made Proton Calendar simple and easy to use with seamless integration across your devices. With the Proton Calendar beta, you can:
- Create, edit, and delete events across devices
- Set reminders
- Send and respond to event invitations (web only for now)
- Set up recurring events annually, monthly, weekly, daily, or on an interval of your choice
- Also available in dark mode!
Proton Calendar is integrated with Proton Mail. You can respond to event invitations you receive in Proton Mail web, including invitations from Google or Microsoft calendars.
You can also import your existing calendar to Proton Calendar with only a couple of clicks.
Make every day safer with our end-to-end encryption
Millions of people around the world use Proton Mail every day to protect the privacy and security of their messages. That’s why we are using the same end-to-end encryption to keep your life events private, safe, and secure.
When you create an event in the Proton Calendar, your event’s details, including the title, description, location, and people you invite, are encrypted on your device so no one, not even us, can see them. Whether you’ve scheduled a doctor’s appointment, a bank visit, or a meet-up with old friends, you control who gets access to that information.
Learn more about how Proton Calendar protects your data(new window)
Thank you for choosing Proton Calendar beta, and don’t forget to share your feedback(new window).
Feel free to share your feedback and questions with us via our official social media channels on Twitter(new window) and Reddit(new window).