
Avast has just released a decryption tool that will help AtomSilo and LockFile ransomware victims recover some of their files for free without having to pay a ransom.
Avast released another decryption tool earlier today to help Babuk ransomware victims recover their files for free.
As the Czech cybersecurity software firm explained, this decryptor may not be able to decrypt files with unknown, proprietary, or with no format at all.
"During the decryption process, the Avast AtomSilo decryptor relies on a known file format in order to verify that the file was successfully decrypted. For that reason, some files may not be decrypted," Avast's Threat Intelligence Team said.
The decryptor works for both ransomware strains because they are very similar, even though the groups deploying them on victims' networks use different attack tactics.
Avast Threat Labs said this ransomware decryptor was created in collaboration with RE - CERT malware analyst Jiří Vinopal, who found a weakness in the AtomSilo ransomware earlier this month.
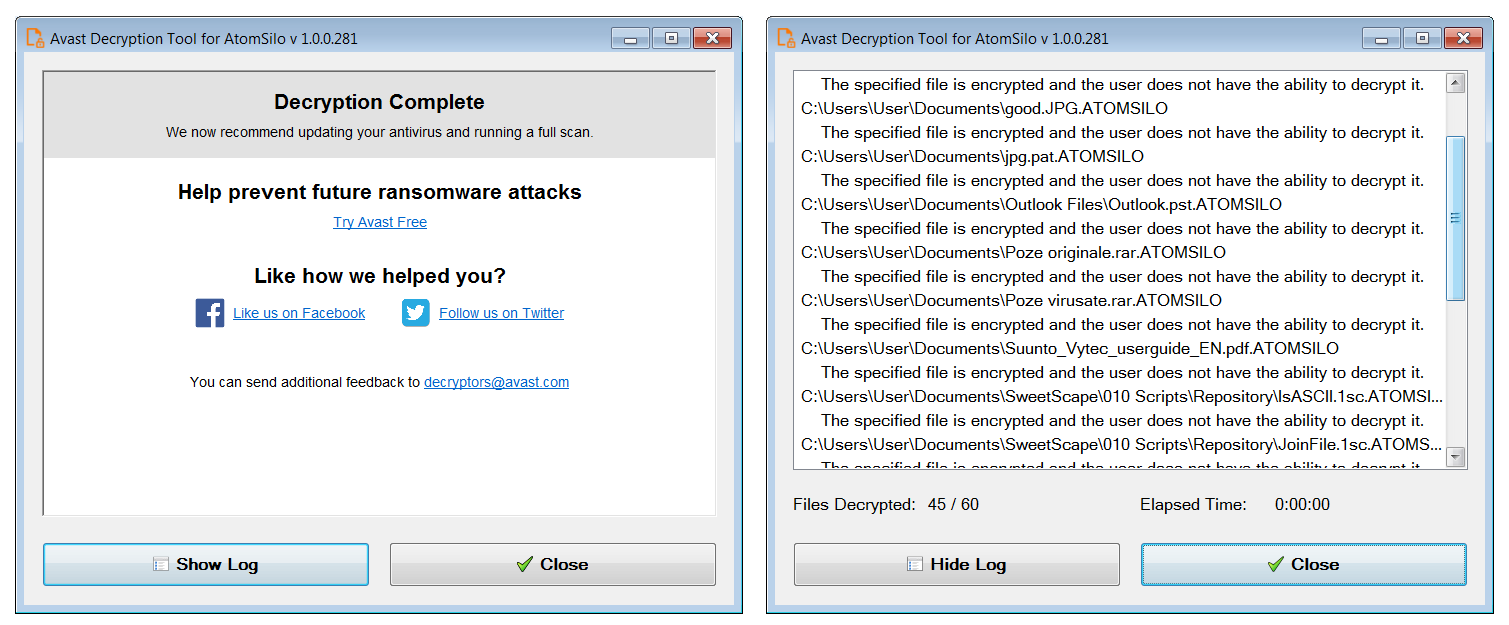
AtomSilo and LockFile victims can download the decryption tool from Avast's servers and decrypt entire disk partitions using the instructions displayed within the decryptor's UI.
BleepingComputer tested the tool and recovered files encrypted with an Atom Silo sample using Avast's free decryptor.
The LockFile ransomware operation was first seen in July 2021 after the gang was spotted taking over Windows domains and encrypting devices after exploiting servers unpatched against the ProxyShell and PetitPotam vulnerabilities.
When encrypting files, LockFile ransomware will append the .lockfile extension to the encrypted files' names and drop ransom notes named using the '[victim_name]-LOCKFILE-README.hta' format.
Of particular interest is that LockFile's color scheme and ransom note layout are very similar to the LockBit ransomware. However, there does not appear to be any relation between the two groups.
Atom Silo is a newly spotted ransomware gang whose operators have recently targeted Confluence Server and Data Center servers vulnerable against a now patched and actively exploited bug.
The ransomware used by Atom Silo is almost identical to LockFile, according to SophosLabs researchers.
However, Atom Silo operators use novel techniques that make it extremely difficult to investigate their attacks, including side-loading malicious dynamic-link libraries that disrupt endpoint protection solutions.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now