
Image: Ivan Diaz
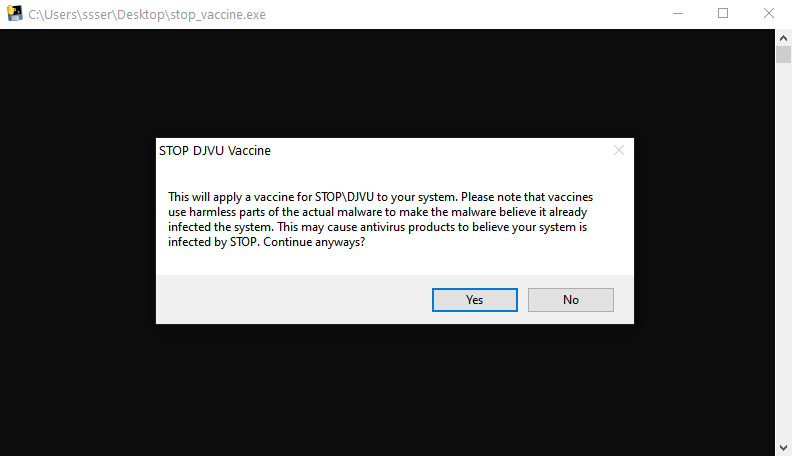
German security software company G DATA has released a vaccine that will block STOP Ransomware from encrypting victims' files after infection.
"This tool does not prevent the infection itself. STOP ransomware will still place ransom notes and may change settings on the systems," G DATA malware analysts Karsten Hahn and John Parol explained.
"But STOP ransomware will not encrypt files anymore if the system has the vaccine. Instead of a personal ID, the ransom notes will contain a string that files were protected by the vaccine."
You can download the STOP Ransomware vaccine here, as a compiled .EXE or Python script.
This vaccine may cause your security software to believe your system is infected since it works by adding files the malware usually deploys on infected systems to trick the ransomware the device was already compromised.
While a decryptor was also released for STOP Ransomware in October 2019 by Emsisoft and Michael Gillespie to decrypt files encrypted by 148 variants for free, it no longer works with newer variants. Hence, G DATA's vaccine is your best bet if you want protection against this ransomware strain.
However, since threat actors commonly bypass vaccines after they are released, this vaccine may stop working for future versions of this ransomware.
Therefore, after applying the vaccine, you should ensure that your important files are also backed up!
STOP Ransomware — the most active ransomware nobody talks about
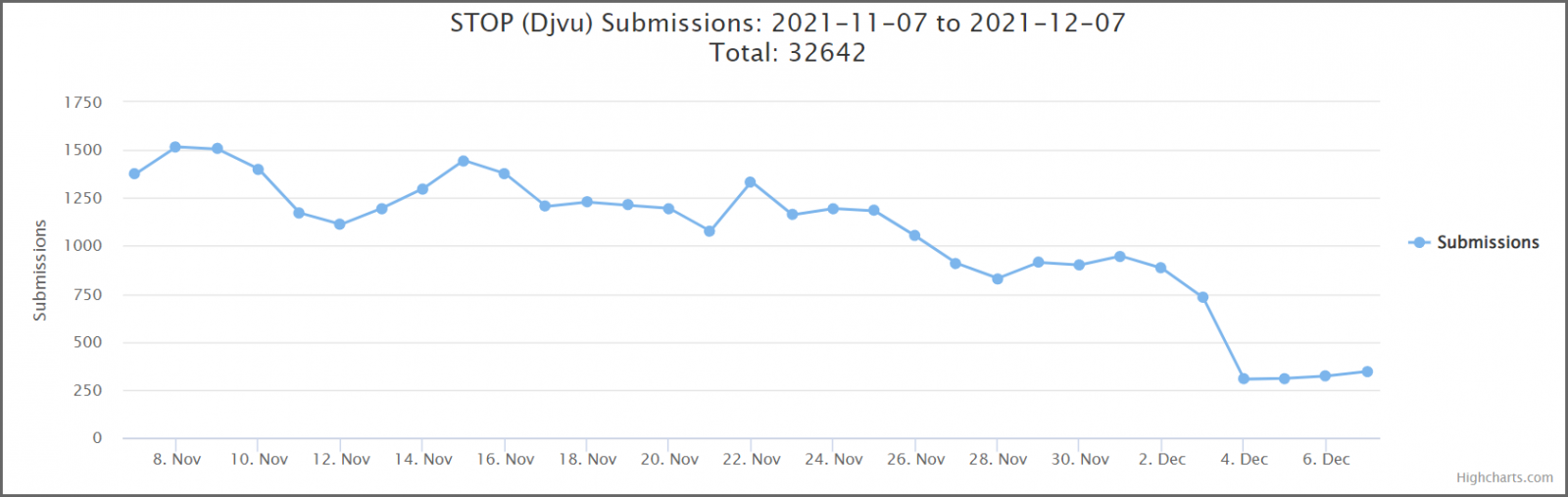
While other ransomware strains get the most media attention, STOP ransomware has constantly been behind the most significant slice of ID Ransomware submissions and support requests on BleepingComputer's forums in recent years.
Out of thousands of ID Ransomware submissions per day during high ransomware activity, anywhere between 60 and 70 % are STOP ransomware submissions.
This is because this ransomware mainly targets home users through shady sites and adware bundles that push malicious software cracks or adware bundles disguised as free programs.
The latter usually install a wide range of unwanted software onto a user's computer, and, more often than not, one of the programs installed is malware such as STOP Ransomware.
Cracks reported to have been used in STOP Ransomware delivery include KMSPico, Cubase, Photoshop, and antivirus software.
Besides using this deployment method, STOP is just your ordinary ransomware, which encrypts files, appends an extension, and drops a note asking for a ransom ranging from $500 to $1000.
However, what makes it so successful is the massive amount of variants constantly being released to avoid detection.



Comments
Mac_Jones - 2 years ago
Wow! That's nice!
Anyway, come on people wake up! Get a grip! this Goddamn Ransomware needs serious attention to the public . it should be on the Top Most Wanted list of the FBI, Interpol, and other Agencies in order to arrest these spineless cowards .
Some-Other-Guy - 2 years ago
No, you just need to secure your computer
I can run Windows XP-SP2 online without a single security update in a full admin account without ever having a single malware or ransomware problem
Why can't "you" do that with a fully updated Windows 10 or 11 installation?
Why?
The problem is between the keyboard and chair
Fix that!
Mac_Jones - 2 years ago
NP i'll see what i can do but first you need to adjust your attitude as the way you talking to me will not gonna help fix that sh*t (calm down ok) .
Two things is either we have to keep ourselves quiet and wait for good news or we talk none-sense for nothing . other than that I don't have time to chat with you . and that's the bottom line because Mac_Jones said so !
PS: my keyboard and chair looks ok maybe yours is not mудак .
Some-Other-Guy - 2 years ago
The point is......
I took serious action against ransomware and all other malware affecting Windows way back in 2014
There is no longer a ransomware problem for anyone who knows how to stop it and no further action needs to be taken on the matter
So YOU Get a Grip and fix the problem at YOUR end!
The FBI, Interpol, and other Agencies are not relevant to fixing the problem and cannot fix it
Mac_Jones - 2 years ago
we'll then don't bother me again, Good luck out there whoever[Some-Other-Guy] you are . you'll need it :P
Some-Other-Guy - 2 years ago
Already have it!
There is no ransomware problem here
Perhaps you were not paying attention again
Mac_Jones - 2 years ago
i know that (^^)b, look i'm not here to argue but i said those words from the beginning because me as a victim(3 months past no good news) i have to express my frustrations towards Incompetent agencies ala protesting . i hope THEY are gonna listen to us .
stevgoogy - 4 months ago
Hello has anyone managed to decrypt malware with an online key specifically the djvu ransomware